Researchers Show How Networks Can Be Hacked from a Lightbulb
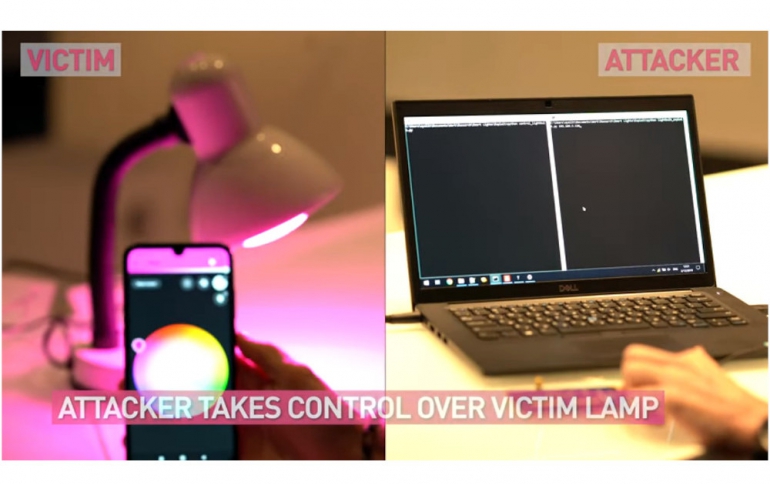
Security researchers showed how a threat actor could exploit an IoT network (smart lightbulbs and their control bridge) to launch attacks on conventional computer networks in homes, businesses or even smart cities.
Check Point’s researchers focused on the market-leading Philips Hue smart bulbs and bridge, and found vulnerabilities (CVE-2020-6007) that enabled them to infiltrate networks using a remote exploit in the ZigBee low-power wireless protocol that is used to control a wide range of IoT devices.
With the help of the Check Point Institute for Information Security (CPIIS) in Tel Aviv University, the researchers were able to take control of a Hue lightbulb on a target network and install malicious firmware on it. From that point, they used the lightbulb as a platform to take over the bulbs’ control bridge, and attacked the target network as follows:
- The hacker controls the bulb’s color or brightness to trick users into thinking the bulb has a glitch. The bulb appears as ‘Unreachable’ in the user’s control app, so they will try to ‘reset’ it.
- The only way to reset the bulb is to delete it from the app, and then instruct the control bridge to re-discover the bulb.
- The bridge discovers the compromised bulb, and the user adds it back onto their network.
- The hacker-controlled bulb with updated firmware then uses the ZigBee protocol vulnerabilities to trigger a heap-based buffer overflow on the control bridge, by sending a large amount of data to it. This data also enables the hacker to install malware on the bridge – which is in turn connected to the target business or home network.
- The malware connects back to the hacker and using a known exploit (such as EternalBlue), they can infiltrate the target IP network from the bridge to spread ransomware or spyware.
The research was disclosed to Philips and Signify (owner of the Philips Hue brand) in November 2019. Signify confirmed the existence of the vulnerability in their product, and issued a patched firmware version (Firmware 1935144040) which is now available on their site.
In a joint decision with Signify, Check Point decided to postpone the release of the full technical details of the research in order to allow Philips Hue clients to have enough time to safely update their products to the latest version.