Researchers Say 1 Million Google Accounts Breached by "Gooligan"
Security researchers revealed and alarming malware campaign. The attack campaign, named Gooligan, breached the security of over one million Google accounts. The number continues to rise at an additional 13,000 breached devices each day.
Research firn Check Point exposes how the malware roots infected devices and steals authentication tokens that can be used to access data from Google Play, Gmail, Google Photos, Google Docs, G Suite, Google Drive, and more.
Gooligan is a new variant of the Android malware campaign found in the SnapPea app last year.
Check Point has reached out to the Google Security team with information on this campaign, and security researchers are working closely with Google to investigate the source of the Gooligan campaign.
Gooligan potentially affects devices on Android 4 (Jelly Bean, KitKat) and 5 (Lollipop), which is over 74% of in-market devices today. About 40% of these devices are located in Asia and about 12% are in Europe.
Check Point identified tens of fake applications that were infected with this malware. Check Point has launched a free online tool that can be used to check if your device has been breached.
If your account has been breached, you should perform a clean installation of an operating system on your mobile device (a process called "flashing"). Change your Google account passwords immediately after this process.
Traces of the Gooligan malware code have been spoted in dozens of legitimate-looking apps on third-party Android app stores. These stores are an attractive alternative to Google Play because many of their apps are free, or offer free versions of paid apps. However, the security of these stores and the apps they sell aren't always verified. Gooligan-infected apps can also be installed using phishing scams where attackers broadcast links to infected apps to unsuspecting users via SMS or other messaging services.
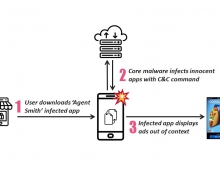
The infection begins when a user downloads and installs a Gooligan-infected app on a vulnerable Android device. After an infected app is installed, it sends data about the device to the campaign's Command and Control (C&C) server.
Gooligan then downloads a rootkit from the C&C server that takes advantage of multiple Android 4 and 5 exploits including the well-known VROOT (CVE-2013-6282) and Towelroot (CVE-2014-3153). These exploits still plague many devices today because security patches that fix them may not be available for some versions of Android, or the patches were never installed by the user. If rooting is successful, the attacker has full control of the device and can execute privileged commands remotely.
After achieving root access, Gooligan downloads a new, malicious module from the C&C server and installs it on the infected device. This module injects code into running Google Play or GMS (Google Mobile Services) to mimic user behavior so Gooligan can avoid detection, a technique first seen with the mobile malware HummingBad. The module allows Gooligan to:
Steal a user's Google email account and authentication token information
Install apps from Google Play and rate them to raise their reputation
Install adware to generate revenue
Ad servers, which don't know whether an app using its service is malicious or not, send Gooligan the names of the apps to download from Google Play. After an app is installed, the ad service pays the attacker. Then the malware leaves a positive review and a high rating on Google Play using content it receives from the C&C server.