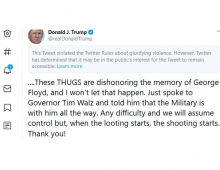
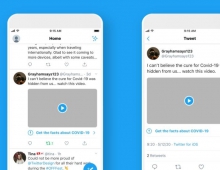
Twitter Resolves "onMouseOver" Flaw
Twitter on Tuesday was notified of a security exploit which was immediately fixed. However, some time later a related issue came up tied to hovercards, which was also fixed.
The security exploit that caused problems was caused by cross-site scripting (XSS). Cross-site scripting is the practice of placing code from an untrusted website into another one. In this case, users submitted javascript code as plain text into a Tweet that could be executed in the browser of another user.
Twitter discovered and patched this issue last month. However, a recent site update (unrelated to new Twitter) unknowingly resurfaced it.
Early on Tuesday, a Twitter user noticed the security hole and took advantage of it on Twitter.com. First, someone created an account that exploited the issue by turning tweets different colors and causing a pop-up box with text to appear when someone hovered over the link in the Tweet. This is why folks are referring to this an "onMouseOver" flaw -- the exploit occurred when someone moused over a link.
Other users took this one step further and added code that caused people to retweet the original Tweet without their knowledge.
This exploit affected Twitter.com and did not impact the company's mobile web site or mobile applications. The vast majority of exploits related to this incident fell under the prank or promotional categories, Twitter said. Although users may still see strange retweets in their timelines caused by the exploit, the company is not aware of any issues related to it that would cause harm to computers or their accounts. Twitter says that there is no need to change passwords because user account information was not compromised through this exploit.
"We?re not only focused on quickly resolving exploits when they surface but also on identifying possible vulnerabilities beforehand. This issue is now resolved. We apologize to those who may have encountered it," Twitter added.
Twitter discovered and patched this issue last month. However, a recent site update (unrelated to new Twitter) unknowingly resurfaced it.
Early on Tuesday, a Twitter user noticed the security hole and took advantage of it on Twitter.com. First, someone created an account that exploited the issue by turning tweets different colors and causing a pop-up box with text to appear when someone hovered over the link in the Tweet. This is why folks are referring to this an "onMouseOver" flaw -- the exploit occurred when someone moused over a link.
Other users took this one step further and added code that caused people to retweet the original Tweet without their knowledge.
This exploit affected Twitter.com and did not impact the company's mobile web site or mobile applications. The vast majority of exploits related to this incident fell under the prank or promotional categories, Twitter said. Although users may still see strange retweets in their timelines caused by the exploit, the company is not aware of any issues related to it that would cause harm to computers or their accounts. Twitter says that there is no need to change passwords because user account information was not compromised through this exploit.
"We?re not only focused on quickly resolving exploits when they surface but also on identifying possible vulnerabilities beforehand. This issue is now resolved. We apologize to those who may have encountered it," Twitter added.